Source: Moeomu’s blog
SafeSEH Introduction
Work
- Check if the exception handling chain is located in the current program’s stack. If it is not in the current stack, the program will terminate the exception handling function call.
- Check if the exception handler pointer points to the current program’s stack. If it points to the current stack, the program will terminate the exception handler call.
- After the first two checks are passed, the program calls a brand new function
RtlIsValidHandler()to verify the validity of the exception handling function, and this function does the following- Determine if the address of the exception handling function is in the memory space of the loaded module, if it belongs to the memory space of the loaded module, the validation function will perform the following checks in turn.
- Determine whether the program has set the
IMAGE_DLLCHARACTERISTICS_NO_SEHflag. If this flag is set, exceptions within this program will be ignored. So when this flag is set, the function returns the checksum failure directly. - Detects if the program contains a security
S.E.Htable. If the program contains the safetyS.E.Htable, the current exception handling function address is matched with this table, and a successful match returns a check success, a failed match returns a check failure. - Determine whether the program sets the
ILonlyflag. If this flag is set, it means that the program contains only the .NET compiled intermediate language and the function directly returns a checksum failure. - Determine if the address of the exception handling function is located on a non-executable page. When the address of the exception handler is on a non-executable page, the check function will check whether
DEPis enabled or not, and return a successful check if the system does not enableDEP, otherwise the program throws an access violation exception.
- Determine whether the program has set the
- If the address of the exception handling function is not included in the memory space of the loaded module, the check function will directly perform
DEPrelated detection, and the function will perform the following checks in turn.- Determine if the address of the exception handling function is located on a non-executable page (non-executable page). When the address of the exception handling function is located on the non-executable page, the check function will check whether
DEPis on or not, if the system is not onDEP, the check will return to success, otherwise the program throws an access violation exception. - Determine whether the system allows jumping to execute outside the memory space of the loaded module, if it does, then return the validation success, otherwise return the validation failure.
- Determine if the address of the exception handling function is located on a non-executable page (non-executable page). When the address of the exception handling function is located on the non-executable page, the check function will check whether
- Determine if the address of the exception handling function is in the memory space of the loaded module, if it belongs to the memory space of the loaded module, the validation function will perform the following checks in turn.
Flowchart of
RtlIsValidHandler()function detection

Feasibility analysis
- Exception handling function is located outside the memory range of the load module and DEP is closed
- The exception handling function is located within the memory range of the load module, the corresponding module is not SafeSEH enabled (the SafeS.E.H table is empty), and the corresponding module is not pure IL
- The exception handling function is located in the memory range of the loaded module, the corresponding module is SafeSEH enabled (the SafeS.E.H table is not empty), and the address of the exception handling function is included in the SafeS.E.H table
Ultimate solution: arrange the shellcode in the heap area, even if SEH verification is not feasible it will still be called
Bypass SEH in the heap
Code
|
|
Description
- Put shellcode into the heap area
- Stack overflow, overwriting the SEH chain address to the shellcode address in the heap area
- Call SEH and subsequently trigger shellcode automatically
Note: pay attention to the 0 case, string copy is encountering 0 cutoff
Bypass SafeSEH by using a module that is not SafeSEH enabled
Code
|
|
Experimental ideas
- Use VC6 to compile SEH_NOSafeSEH_JUMP.DLL, so that SEH_NOSafeSEH_JUMP.DLL will not enable SafeSEH, using release mode
- Use VS2008 to compile SEH_NOSafeSEH.EXE, so that SEH_NOSafeSEH.EXE will be SafeSEH enabled, using release mode, and compile with no optimization settings.
- The test function of SEH_NOSafeSEH.EXE has an obvious stack overflow vulnerability, which also requires that there be no zeros in the shellcode
- SEH is overwritten to create a divide by 0 exception, hijacking the exception handling process
Advance processing
- Since the default loading base address of the DLL compiled by
VC++ 6.0is0x10000000, if it is used as the loading base address of the DLL, the address of thepop pop retninstruction in the DLL may contain0x00, which will truncate the string when we do strcpy operation and affect the copy of our shellcode, so in order to To facilitate the test we need to reset the base address. Select “Project → Settings” in the top menu, then switch to the “Connections” tab and add/base:" 0x11120000"in the “Project Options” input box.
Problems encountered
- The springboard will jump to the first 4 bytes of the address in the shellcode, so you should put jmp here
- The program compiled by
VS 2008will press-2(-1underVC++ 6.0) atSecurity Cookie+4when it enters the function containing__try{}, and the program will press-2(-1underVC++ 6.0) when it enters the__try{}area according to the__try{}block is modified to a different value depending on the position of the__try{}block in the function. For example, if there are two__try{}blocks in the function, this value will be modified to0when entering the first__try{}block, and to1when entering the second. If an exception occurs in the__try{}block, the program will call the corresponding__except()to handle it based on this value, and the value in this position will be modified to-2again after the process is finished; if no exception occurs in the__try{}block, the value will also be modified back to-2when the program leaves the__try{}block. 2. Of course there are other uses for this value in exception handling. We just need to know that our shellcode may be corrupted due to its presence, so we should put eight bytes ofNOP` after the module address as a protection measure. - There is a four-byte discordance between
retnback to the stack address space and the shellcode body, so we need to jump to the shellcode and execute
Bypass SafeSEH by using addresses other than the loaded module
SafeSEH is enabled by default for all modules
Springboard
| Address | Disassembly code |
|---|---|
| call/jmpdword ptr[esp+0x8] | |
| call/jmpdword ptr[esp+0x14] | |
| call/jmpdword ptr[esp+0x1c] | |
| call/jmpdword ptr[esp+0x2c] | |
| call/jmpdword ptr[esp+0x44] | |
| call/jmpdword ptr[esp+0x50] | |
| call/jmp dword ptr[ebp+0xc] | |
| call/jmp dword ptr[ebp+0x24] | |
| call/jmp dword ptr[ebp+0x30] | |
| call/jmp dword ptr[ebp-0x4] | |
| call/jmp dword ptr[ebp-0xc] | |
| call/jmp dword ptr[ebp-0x18] |
Code
|
|
Vulnerability Execution Flow
- Buffer overflow overrides SEH chain to handle addresses outside the module to bypass SafeSEH
- A
call [ebp+0x30]instruction is found at0x00290B0B, which is used as a springboard to jump into the shellcode
Problems faced by ####
0x00290B0Bcontains byte0x00, strcpy copy will terminate when it encounters it
Solution: 00 can not be missing, let it become the end of shellcode
- The same problem as in the previous section, the program compiled by
VS 2008, when entering the function containing__try{}will be pressed into-2at the location ofSecurity Cookie+4, it will destroy the shellcode, so we need to skip it, it will overwrite the location code written in, so We need to use the 12 bytes below it to jump to the entrance of the real shellcode, so we need to use two jumps to jump to the entrance, the first jump is to jump to the long jump, and the second long jump is to jump to the shellcode
Using Adobe Flash Player ActiveX control to bypass SafeSEH
Principle
Actually this method is to bypass SafeSEH by using the browser version of the SafeSEH module which is not enabled. Flash Player ActiveX does not support SafeSEH in versions before 9.0.124, so if we can find a suitable springboard address in this control, we can bypass SafeSEH completely.
- Flash plugin as a module to find the springboard, because it does not have SafeSEH enabled
- We construct code modules that cause stack overflow vulnerabilities
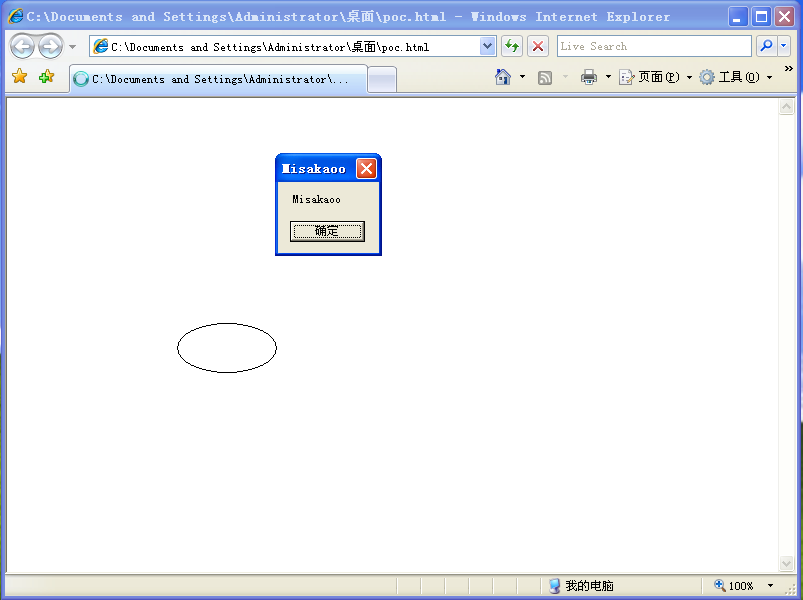
- Constructing a POC html page to call the vulnerable code we constructed
- After our code module overflows and overwrites the SEH chain, it will jump to the Flash code springboard we have prepared
- The shellcode from the Flash code springboard jumps into our stack area
- The exploit is successful
code
- Download IE7-for-XP-x86-Chinese installer
- Download the Flash Player ActiveX
v9.0.124installer - Create an MFC ActiveX control, I packaged a copy of the project I created here download
- Detailed setup diagram

- Use Unicode character set, disable compile optimization option, use MFC in static library, compile with release version
|
|
- UUID of
CVulnerAX_SEHCtrl's class informationinVulnerAX_SEH.idl:ACA3927C-6BD1-4B4E-8697-72481279AAEC
Other steps
- Register the control:
Regsvr32 path \ control name.ocx - Once registered we can call our function from the web page in the following way
|
|
Trigger vulnerability
Constructing POC pages
|
|
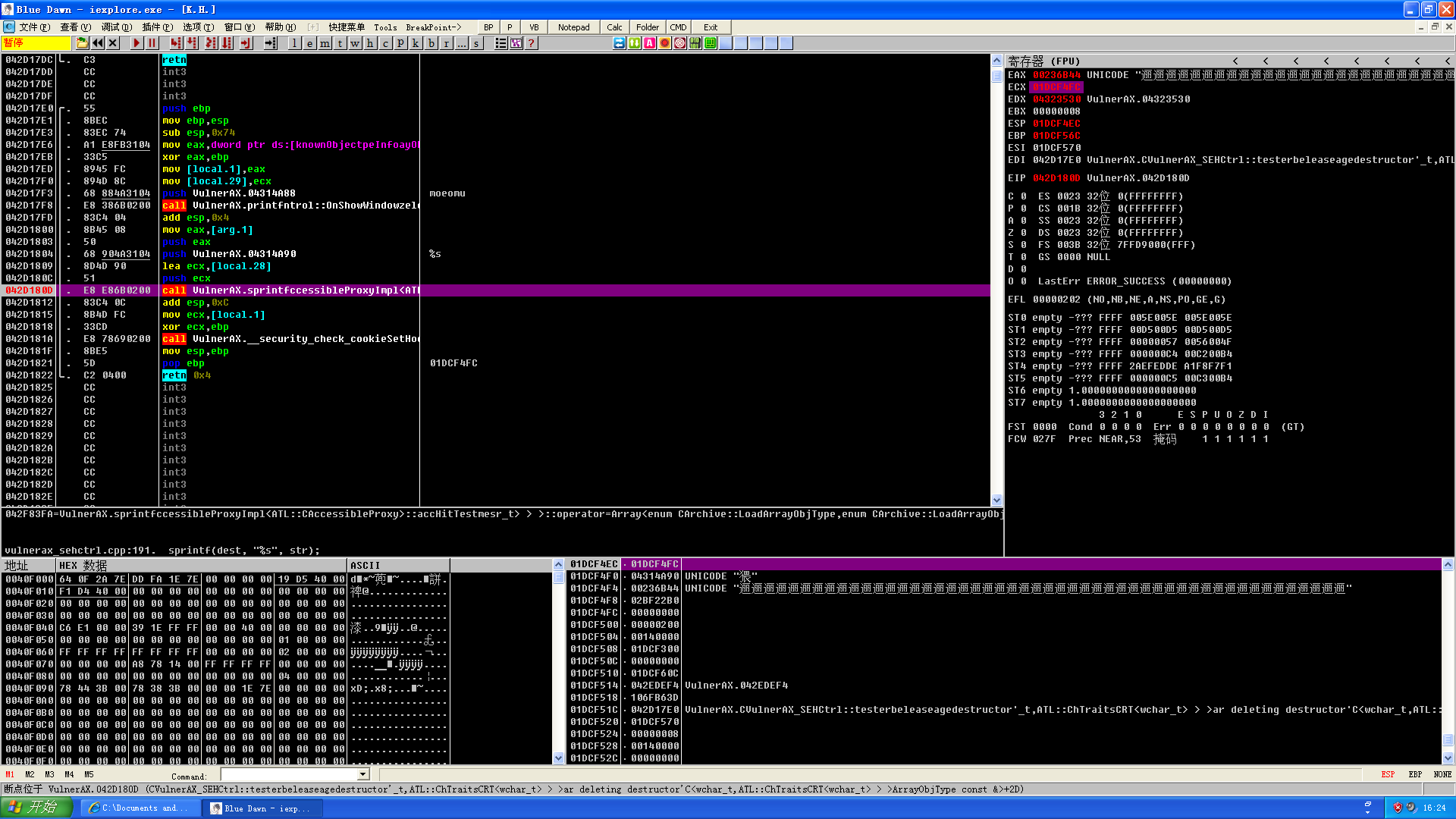
Analysis
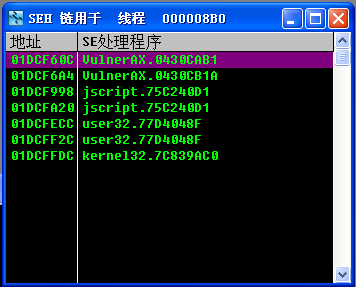
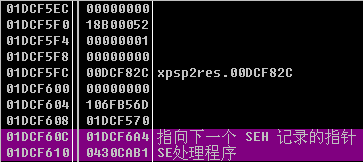
- As shown in the figure, the address
0x01DCF4FCpointed by ecx is the starting address of the overflow string, and the closest exception function address to the top of the stack is located at0x01DCF610, which is calculated to fill0x114which is 276 bytes to cover the exception handling function address, and the 277th-280th bytes can be placed in the springboard
- Using the
OllyFindAddrplugin’sOverflow return address->Find CALL/JMP[EBP+N]option to find the instruction, this experiment found theCALL [EBP+0xC]of0x300B2D1Cas a springboard, as shown in the figure
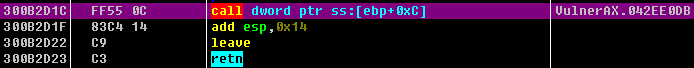
- According to the previous calculation put the springboard address into the shellcode corresponding location, save the POC page, test change the function as follows
|
|
- It is said in the book that at this time the trigger except 0 exception will be transferred to the shellcode springboard, but it seems that the operation is not written in advance, so again compile the plug-in, in the test function to add except 0 operation
- At this point, the successful break at the springboard, the EBP register value is
0x01DCF150, according to the springboard instructions will jump to the springboard address before the 4 bytes, where you can add a jump, and shellcode to the back, as follows
|
|
- The final test function is shown below
|
|
- Successfully executed as shown