Source: Moeomu’s blog
Principle
By requesting a large amount of memory, occupying the 0x0C0C0C0C locations in memory, and placing 0x90 and shellcode in these memories, and finally controlling the program to go to 0x0C0C0C0C for execution. As long as the luck is not so bad that 0x0C0C0C0C0C happens to be located somewhere in the shellcode, the shellcode will be executed successfully
Experiment
Preparation
Environment: System: Windows Vista SP0, DEP Status: Default, Browser: IE7
- Still use the previously used Vulner_AX.dll as the target of the attack
- UUID of
CVulnerAXCtrl's class informationinVulnerAX.idl:ACA3927C-6BD1-4B4E-8697-72481279AAEC
Idea
- We use the Heap spray technique to request 200 1MB memory blocks in memory to counteract the randomization process of ASLR
- Each memory block contains 0x90 padding and shellcode
- After Heap spray we occupy the memory near
0x0C0C0C0C, we just control the program to go to0x0C0C0C0Cfor execution, and after several 0x90 slides we can reach the shellcode range and execute - There is a typical overflow vulnerability in the test function, where the function return address can be overwritten by copying a very long string
- We will overwrite the function return address as
0x0C0C0C0C, after the function execution returns to execution will be transferred to the memory space we apply
Code
|
|
Result
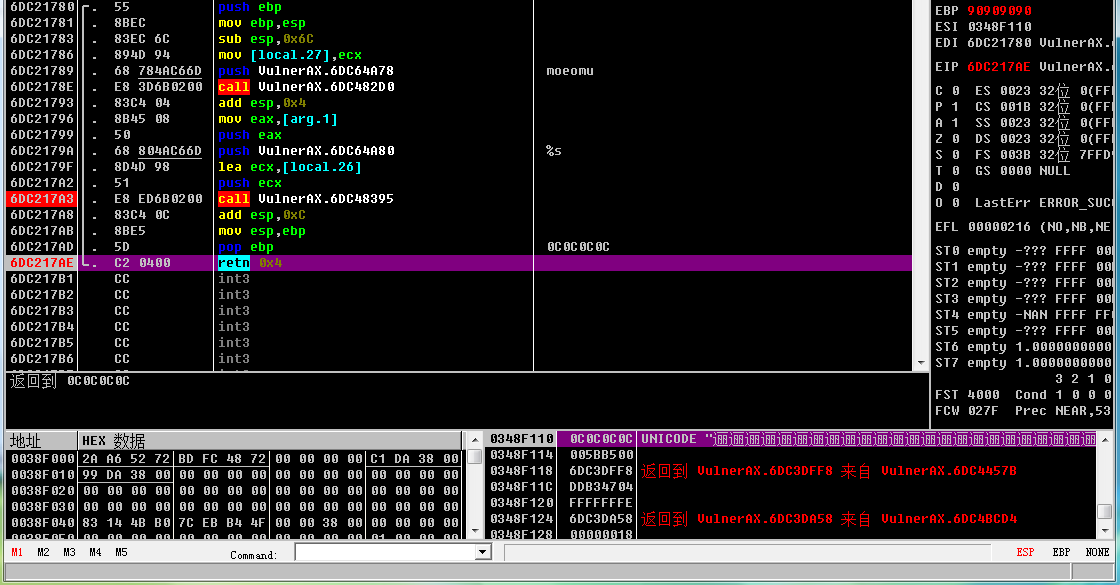
- Successful attack on ASLR, as shown in the figure